As many as 46% of global IT security incidents each year are caused by employees, according to a Kaspersky Lab and B2B International report titled, Human factor in IT security: How employees are making businesses vulnerable from within. In addition, employees hide IT security incidents in 40% of businesses around the world – this figure is as high as 48% for South African businesses.
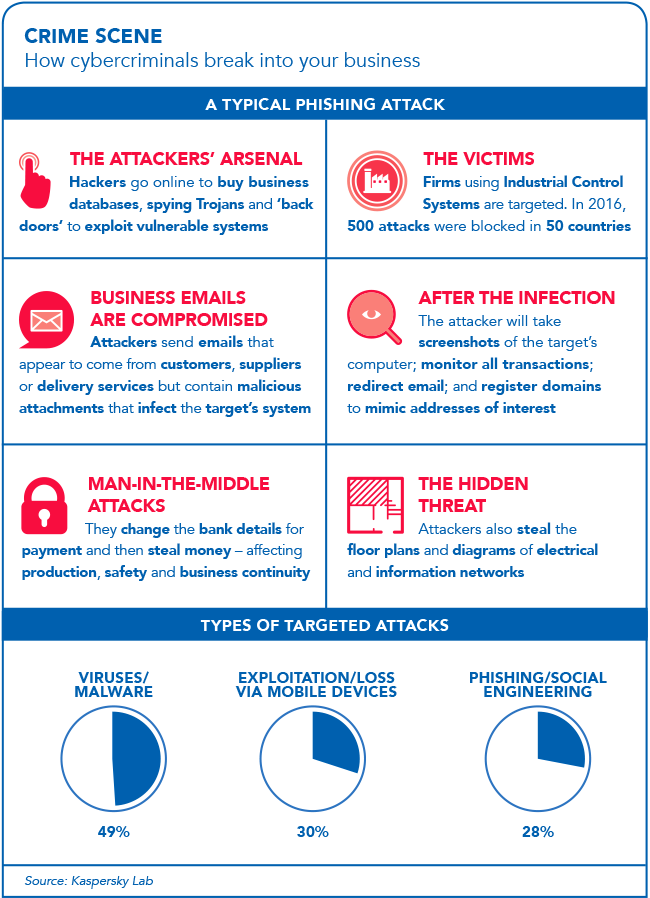
Global research further reveals that as many as one-third of targeted attacks on businesses have phishing or social engineering at their source. This could be as simple as someone in the accounts department opening what they thought was an invoice from one of the company’s contractors, without realising it was hiding a malicious file. Such an act could shut down the entire organisation’s infrastructure and expose it to immense risk.
In years past, phishing emails were easy to spot – the grammar and spelling was terrible, and the communication clearly fraudulent. These days, cybercriminals have become smarter, their spelling has improved, and they have managed to successfully copy the look and feel of legitimate correspondence, such as from banks and other official institutions. If their phishing attempt is a success, they may gain access to the victim’s computer and the computer network on which that machine sits, and in so doing, have an open door into the organisation at which that person works. If they pass through undetected, the organisation is their oyster.
Kalyani Pillay, CEO of the South African Banking Risk Information Centre, says cybercriminals have most certainly upped their game. ‘We hardly ever see people sending out emails that are badly written. They’ve become smarter and more diligent in terms of how they communicate. They’ve also become quite tech savvy in terms of the methods they use to get people to believe they’re communicating with someone else; someone authentic, or someone who they are purporting to be.’
According to Nadezhda Demidova, lead web content analyst at Kaspersky Lab, phishing scams ‘continue to increase in quality and quantity every day and cybercriminals are continuously improving their tactics. They use new technologies and make attacks more complex and less visible for detection by a simple user’. This is due both to the general level of technology development and the fact that more and more ordinary users are beginning to understand the subject well.
*Great Fit | Digital marketing for your business
Demidova notes that phishing content is distributed not only through email but also through social networks, banners, online advertising, text message, messengers and other types of communication. And these days, phishing is just one of the ways cybercriminals try to solicit personal and confidential information, as vishing and smishing have rapidly gained popularity too. Vishing involves voice contact, commonly through a phone call, while smishing uses text-message contact.
Indeed, cybercriminals are masters at using social engineering tactics, says Pillay, and manipulating victims emotionally to get a response. They might ask that you update your FICA information before your accounts are frozen, and so create anxiety or panic, which leads to the person surrendering the requested information, she explains.
Phishing is one of Africa’s most common kinds of cybercrime. Riaan Graham, director of sales, sub-Saharan Africa, at Ruckus Networks, says this is probably because, as development on the continent increases, access to ICT services and networks becomes more prevalent. In addition, corporates might not have the needed security and protocols in place to help their employees, he says. ‘What’s causing Africa to be top of mind is that typically, the education levels of users are not yet on par with developed countries. We are still very much in learning mode in terms of how we properly use email, for example. A lot of people are interacting with email for the first time. These are prime candidates to target.’
Demidova agrees. ‘Many phishing attacks are focused on targeting new and inexperienced users,’ she says, adding that these attacks ‘are not so complex’ and rely ‘on users’ lack of attention and technical illiteracy’.
While phishing is a major problem in Africa, adds Pillay, it’s part of a larger problem – the theft of personal and confidential information and the ability of criminals to harvest that information, regardless of the means.
According to Demidova, mass phishing in Africa is currently aimed primarily at internet-banking users. Kovelin Naidoo, cybersecurity officer at FNB, notes that one of the most prevalent scams currently is remote access fraud, which involves fraudsters remotely taking control of a person’s PC via the internet, to gain access to their banking profile. Fraudsters are employing carefully constructed scamming tactics that can trick even the most vigilant customer if they are not aware of the modus operandi, he explains.

While all the technology used by cybercriminals is the same, emails shared for phishing scams will have different content, says Demidova. ‘They relate to the sphere of activity that the company is engaged in, and are sent – as a rule – to certain users, such as managers, accountants, security personnel and personnel officers.’
She warns that targeted attacks are among the most dangerous types of phishing, especially if the goal is an entire enterprise. ‘Usually, scammers collect preliminary information about the chosen victim and carefully prepare such attacks, which makes them difficult to detect. To prevent such attacks, special attention should be given to training employees in the rules of conduct on the network, as well as using a high-quality protection solution against targeted attacks.’
With regard to attacks on corporate users, Demidova notes that scammers usually use spear phishing. ‘If you believe you have been compromised, you should immediately change the passwords for all your accounts and services; switch on the two-factor authentication process for extra security; and check all of your devices for malware.’
If cybercriminals manage to reach the point where they’ve established a level of trust with an individual’s PC, it is already far too late. ‘They’re in the network,’ says Graham. ‘At that stage it’s very difficult to quarantine the fallout because you’ve already opened up the door, so to speak.’ If this is the case, shut down your PC, take it off the network, and notify the IT department immediately.
One of the main ways to combat phishing threats is simply to improve the online literacy of internet users. Continuous education and training of staff is crucial, as are strict information-security policies. ‘Companies should make it their business to educate their staff and create awareness about some of the risks and compromises that could happen through an individual, but which could affect the entire company,’ says Pillay.
From an IT department perspective, chief information officers and chief information security officers should have cybersecurity as a key priority in terms of managing risk, she advises. ‘They should have proper fire- walls in place, early-warning systems and flags; regularly conduct penetration tests; and check the resilience of their system.’
Without education on cybersecurity, companies could be at risk of personal or reputation damage, which is difficult to fix.